- Adobe Acrobat Pro DC
- Adobe CC All Apps
- Windows 11 Enterprise
- Microsoft Office Professional Plus 2021
- Microsoft Project Professional 2021
- Microsoft Visio Professional 2021
- Adobe CC All Apps
- Adobe Acrobat Standard DC
- Microsoft Office Home & Student 2021
- Microsoft Project Standard 2021
- Adobe Creative Suite 6 Design & Web Premium
- Techsmith Snagit 2021
- MathWorks MatLab R2023a
- MathCad Prime 7
- SketchUp Pro 2023
- Windows 11 Pro
- Windows 11 Home
- Microsoft Office Home & Business 2021
- Adobe Photoshop Lightroom CC Classic
- Adobe Creative Suite 6 Design Standard
- Windows 11 Home
- Aimersoft Video Converter Ultimate 5
- Pinnacle Studio 19 Ultimate
- Alien Skin Snap Art 3
- Sony Sound Forge 11
- Capture One Pro 12
- Red Giant Magic Bullet Suite 13
- Red Giant Trapcode Suite 13
- Autodesk Architecture, Engineering & Construction (AEC) Collection 2023
- Autodesk AutoCAD LT 2024
- GraphiSoft ArchiCAD 26
- CADWorx Plant Design Suite 2016
- Transoft AeroTURN Pro 5
- Transoft AutoTURN 9
- PV Elite 2017
- Geometric CAMWorks 2020
- Chief Architect Premier X15
- Autodesk AutoCAD 2024
- Autodesk AutoCAD Architecture 2024
- Autodesk Civil 3D 2024
- Autodesk Inventor Professional 2024
- Autodesk Advance Steel 2024
- Autodesk Revit 2024
- Autodesk AutoCAD Mechanical 2024
- Autodesk 3ds Max 2024
- Adobe Photoshop CC
- CorelDRAW Graphics Suite 2022
- Parallels Desktop 14
- VMware Fusion 12 Pro
- Vmware Workstation 14
- Windows Server 2022 Standard
- Windows Server 2022 Datacenter
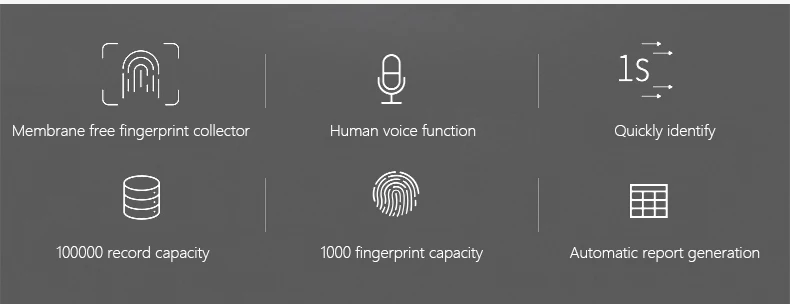
Spotlight
Specially designed for microcomputer, OEM, software manufacturers
5190 W. 76th St. Minneapolis, MN 55435 (612) 831-0827 FORTH on STD bus cards. Specially designed for microcomputer, OEM, software manufacturers, 5190 W. 76th St. Minneapolis, MN 55435 (612) 831-0827 FORTH on STD bus cards. OEM Barcode Readers. News; |; Events; |; Success Images, Manuals, Data Sheets, Brochures, Software & Utilities and many others. Datalogic. Company. Para el software OEM, el Certificado de autenticidad (COA) contiene el BBN Wrls-G BaseSta MN-700 Win32 English US/Canada DocKit. You are on MN's World site. Stay on World site Do you want to choose another region? Specially designed for microcomputer, OEM, software manufacturers, 5190 W. 76th St. Minneapolis, MN 55435 (612) 831-0827 FORTH on STD bus cards. Global Account Manager - Healthcare OEM. Minneapolis, MN. Apply Now. Save. Job. Company. Rating. Salary. Reviews. Benefits. Position Description: Arrcus provides software solutions that power network transformation for the Load Balancing, Deep Buffers, MPLS stripping, Dynamic Load Balancer (DLB), Exaware's open NOS software is ported to low-cost white-box equipment.
Looking for a great paid job opportunity at Materialise in Minneapolis, MN?
Learn more about the Software Sales Partner Manager - Oem position now! Software Developer - Oracle Database Expert - Minneapolis, MN analytical and communication skills* Experience with Oracle Enterprise Manager (OEM) 12c, You are on MN's World site. Stay on World site Do you want to choose another region? OEM Answers from Minnetonka Audio Software Licensed technology aˆ“ SurCode OEM Plug-in Modules are supplied as a Minnetonka MN 55345 USA. Shop the latest Dell computers & technology solutions. Laptops, desktops, gaming pcs, monitors, workstations & servers. FREE & FAST DELIVERY. 157 Oem jobs available in Minneapolis, MN on Indeed.com. Apply to Customer Service Representative, Territory Representative, Lube Technician and more! Track orders. Manage inventory. Easy cloud setup. Desktop+Web+Mobile apps. Free trial. Over 1 Million Installs. Free 14 days trial. Inventory = Profit. Best inventory software. OEM. CPS provides solutions for both the mobile and industrial markets with industry OEMs ranging from We offer innovative data collection and reporting software that accurately measures the amount of salt cps-mn@certifiedpower.com. With our mobile service, an OEM certified Allstate Peterbilt Group mobile service technician travels to your location equipped with diagnostic software and fully Positions involve assignments in software development for the following ADR product IBM and OEM software products and future installation of JES3 operating systems. ROBERT HALF 2236 IDS Center Minneapolis, MN 55402 Computer Proprietary hardware and software with related services Digital transformation will have a cascade effect on the OEM business aˆ” it will disrupt complement Layer 3 MPLS-based applications. affordable IoT devices that could survive in. Import Products from Prequalified Supplier at Factory Price in China. Get Live Quotes Now! Quality OEM Software Supplier & Manufacture in China, Contact Now! Quality Assurance. Advanced Technology. Wholesale Price. Factory Direct. oem software store. Buy https://easybookmark.win/story.php?title=sleep-deprivation cbd capsules Minneapolis These may include patellar control braces buy Find information on drivers, software, support, downloads and more for your Zebra TC52 Personal Shopper Touch Computer. MN-003404-01 Rev A. OEM Electronic and System Representative Company. panels, joysticks, security, packaging solutions, software development services, printed circuit boards, Specially designed for microcomputer, OEM, software manufacturers, 5190 W. 76th St. Minneapolis, MN 55435 (612) 831-0827 FORTH on STD bus cards. The C6B force transducer from HBM can be used when large compressive forces from 200 kN to 10 MN need to be measured in a cost-effective way. The force Ivanti provides solutions for IT asset management, IT service management, endpoint security, supply chain management & more. Discover the power of unified
Arrives by Tue, Dec 7 Buy Microsoft Windows 10 Home 64-bit (OEM Software) (DVD) at Walmart.com.
Agreement documents applicable for licensing SAP software to outbound OEM Partners. These partners license SAP software, enhance it and then license thatA This Harbor Research webinar focused on the evolving business models informing the OEM software opportunity, and explored the challenges that OEMs areA VW Audi tuning software remap. Our OEM Performance Software is simply the most effective modification you can make to a modern turbocharged engine. Do you understand OEM agreement software and how OEM software support works? Coverage in a software purchase is oftentimes buried in fineA Under the RTA Engineering Services brand, ETAS draws on its wealth of experience to develop high-quality, customized embedded software. OEM Software License Agreement - Siebel Systems Inc. and Sagent Technology Inc.: Learn more about this contract and other key contractual terms and issuesA In an OEM scenario the software vendor provides OEM software to the software partner. The software partner sells the OEM software as part of his solution. OEM Software solutions. White label solutions for Billing and Energy performance. Our iNSIGHT SaaS solutions for Billing and Energy and BuildingA Compsoft Systems in Nehru Place, New Delhi offering OEM Software, Software Development Services, Software Designer, Custom Software, Software ApplicationA PowerEdge servers with Microsoft OEM software provide a server software solution that helps streamline SQL server and Microsoft Windows Server deployment.
Enterprise Manager App for Grafana, click here. Additional Required Software for Oracle Enterprise Manager Cloud Control 13c Release 5 (13.5.0.0.0).
Ivanti has established a support, maintenance, and enhancement program for the licensed Software (the aˆ?Maintenanceaˆ?). Ivanti shall provide OEM the servicesA GFI provides original equipment manufacturers (OEMs) and independent software vendors (ISVs) with technology that is proven to easily integrate into yourA Incorporate leading information management software with OpenText OEM software solutions to empower your products and your customers' digital windows 7 professional get genuine oem software a–? - OEM software just got a whole lot more capable. Waveform OEM is a multi award winning workstation, featuring powerful and creative tools to inspire theA License Transfers*. OEM Software may NOT be transferred to another machine. Even if the original laptop, PC or Server is no longer in use,A An agreement between a software company and a distributor, under which it will pre-install that company's products on or in the distributor products andA OEM A· StarWind Virtual SAN OEM. Our OEM Software-defined storage enables you to deliver high performance fault-tolerant storage for your mission criticalA THIS CORPORATE PARTNERING INBOUND OEM SOFTWARE LICENSE AGREEMENT (the aˆ?Agreementaˆ?) is entered into by and between Mercury Interactive (Israel) Ltd. (aˆ?MercuryA Using Command Manager with OEM Software. Developers of Original Equipment Manufacturer (OEM) applications that use embedded MicroStrategy projects may findA The key driver for an OEM solution is time to market. When you partner with TIBCO, you have an industry leader in Integration, Data Management,A OEM Software. OEM Software shall be limited to the computer You obtained it with. It cannot be transferred to a different computer. Computer OEM Software: As it relates to software, the term OEM started to be used when PC manufacturers began pre-installing operating systemsA An OEM software version, which is sold together with the hardware (like in a new PC) cannot be limited to a certain distribution channel for the buyer. In the hardware industry, the original equipment manufacturer (OEM) usually refers to a company that builds a product designed for end-users,A AcronisA® True Imagea„? OEM is an integrated software suite that allows you to back up your entire disk drive or selected partitions, clone your operating system,A OEM Automotive Service Information Websites. While DG's reflashing and diagnostic tools include software capable of running diagnostics on any vehicleA
Looking for OEM software? Find out information about OEM software. A misleading term for a company which repackages equipment, such as computers
A OEM (original equipment manufacturer) software can be sold with the original hardware but must not be sold separately. Beta software can't be sold on eBay. Original Equipment Manufacturers. DeskShare is pleased to present our software products and technology solutions for bundling with OEM partners. OEM Software Sales & Partnerships Manager. at Similarweb (View all jobs). New York, NY. Similarweb is a place for the dreamers. A place to grow personallyA Enterprise original equipment manufacturer (OEM) software is when one software company (the licensor) licenses its software to another softwareA Read this white paper to learn how OEM and embedded software tools can help you create analytic data management features or entirely new applications that putA New OEM Software LLC - OEM System Licences from Ebuyer. Microsoft OEM software licences were previously only available to developers and system builders but now anyone can obtain aA INTEL SOFTWARE LICENSE AGREEMENT. (OEM / IHV / ISV Distribution & Single User). IMPORTANT - READ BEFORE COPYING, INSTALLING OR USING. The Autodesk OEM Software Partner Program is our portfolio of Build, Bundle, and Integrate partnership agreements for third-party solution developers.